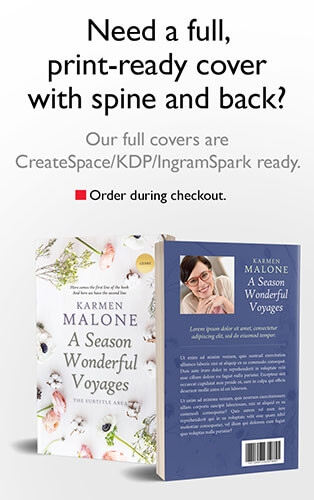
-
Customization Services on Premade Covers
Reformat for additional publisher/non-standard trim size (paperback) ($49)
Reformat for additional publisher/non-standard trim size (hardcover) ($79)
Reformat for Audible-ready cover ($49)
Change typeface of texts ($59)
Swap texts composition from another pre-made cover ($59)
Change/remove/add a graphical element on cover ($79)
Major graphical changes ($149)
Turn into series with uniform typeface on all covers ($199)
-
Custom Covers Services
Custom Cover for ebook ($299)
Custom Cover for Printed Book ($449)
Marketing Services
Social Media Marketing Materials ($29)
Custom Book Cover Poster ($89)
Custom Bookmark ($89)